Solitics’ Security & Compliance
Solitics sets a new standard by offering a single platform that incorporates extensive BI capabilities together with real-time customer engagement automation and personalization
At Solitics, our Security layout is designed to uphold the confidentiality, integrity, and availability of all computer and data communication systems, aligning with essential legislative, industry, and contractual requirements
Our policies, procedures, and standards are grounded in the framework provided by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), specifically ISO/IEC 27001. Furthermore, we ensure the robustness of our security measures through periodic audits conducted by an independent third-party body, validating our compliance with industry-leading standards.
Solitics is compliant with the following industry standards:

GDPR
Solitics proudly complies with the European Union’s Global Data Protection Regulation (GDPR), ensuring the highest standards in data protection. This commitment underscores our dedication to safeguarding the privacy and data rights of individuals within the EU, providing assurance to our customers and partners.
Read Solitics privacy policies.

ISO/IEC 27001:2013
Solitics holds ISO/IEC 27001 certification, an internationally recognized standard for information security. This certification affirms our commitment to best practices in establishing, maintaining, and enhancing an information security management system. It also demonstrates our dedication to assessing and addressing information security risks, tailored to the specific needs of Solitics and our valued customers. You can verify our ISO/IEC 27001 certification Request Doc. Your security is our priority!

SOC 2
Solitics is proud to be SOC 2 Type II audited, a rigorous auditing standard developed by the American Institute of CPAs (AICPA). This certification ensures that we meet stringent criteria for managing customer data based on five “trust service principles”. By complying with SOC 2 Type II requirements, we demonstrate our unwavering commitment to maintaining the highest levels of security and operational effectiveness. SOC 2 Type II Audit report provides our clients with the assurance that their data is handled with the utmost care and precision. You can request our SOC 2 Type II audit report by clicking the “Request Doc” button. Your trust is our commitment!
Select report
Request Certificate
Get more info on Solitics’ solution, product and pricing
Select report
Request Certificate
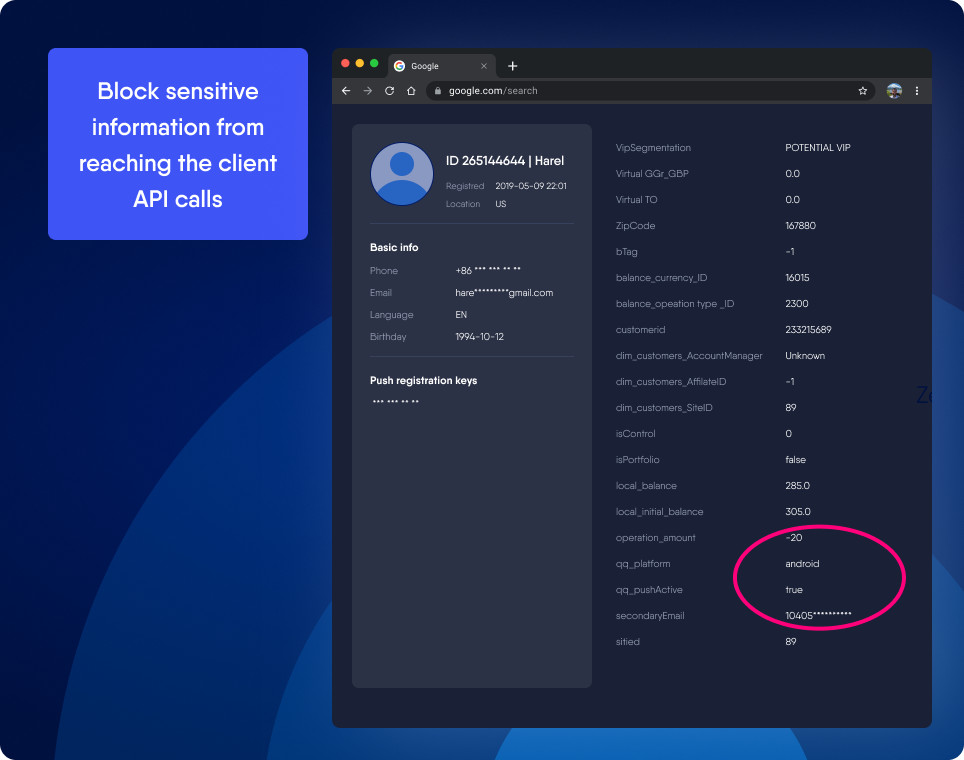
Get more info on Solitics’ solution, product and pricingSensitive data leakage protection
-
Autonomous Sensitive Data Filtering
-
Sensitive Data Filtering
-
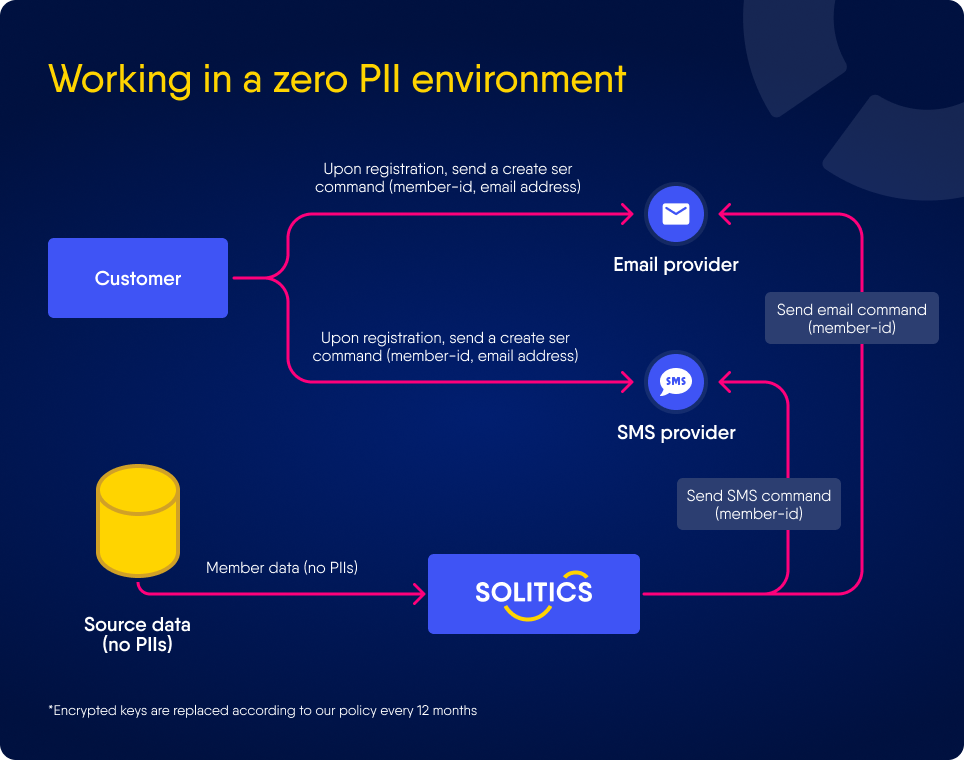
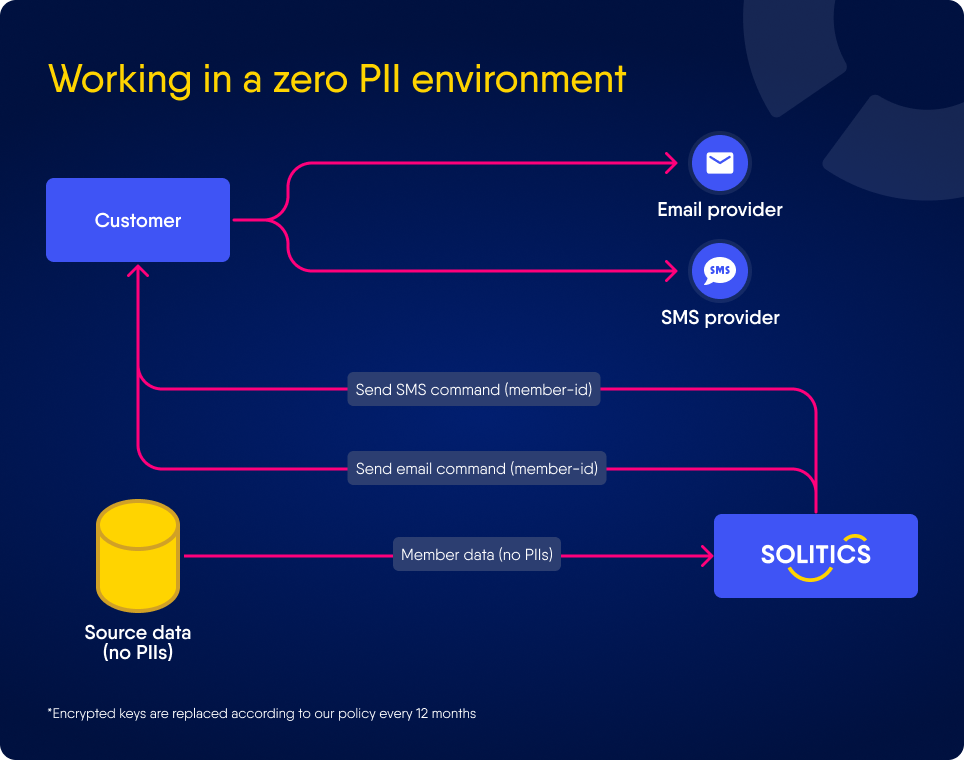
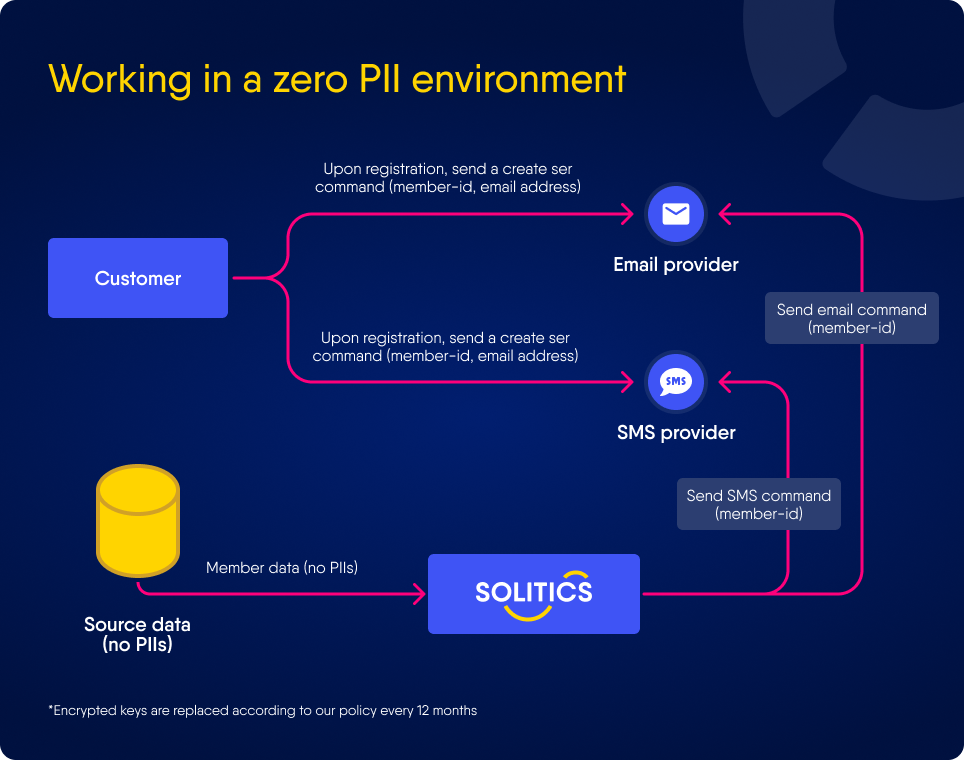
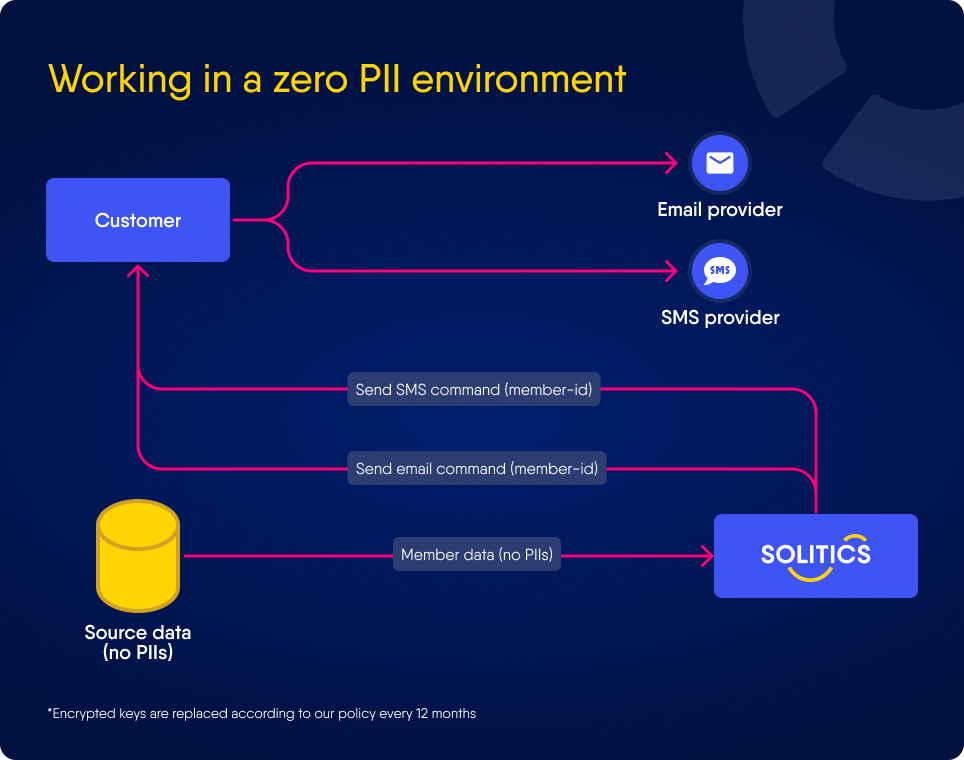
Zero PII Environment - Mode 1
-
Zero PII Environment - Mode 2
Access control
-
Extensive Audit Log
-
Role Based Access Control
-
MFA For users and APPs
-
LDAP / OPENID / SAML connectivity
Data encryption
-
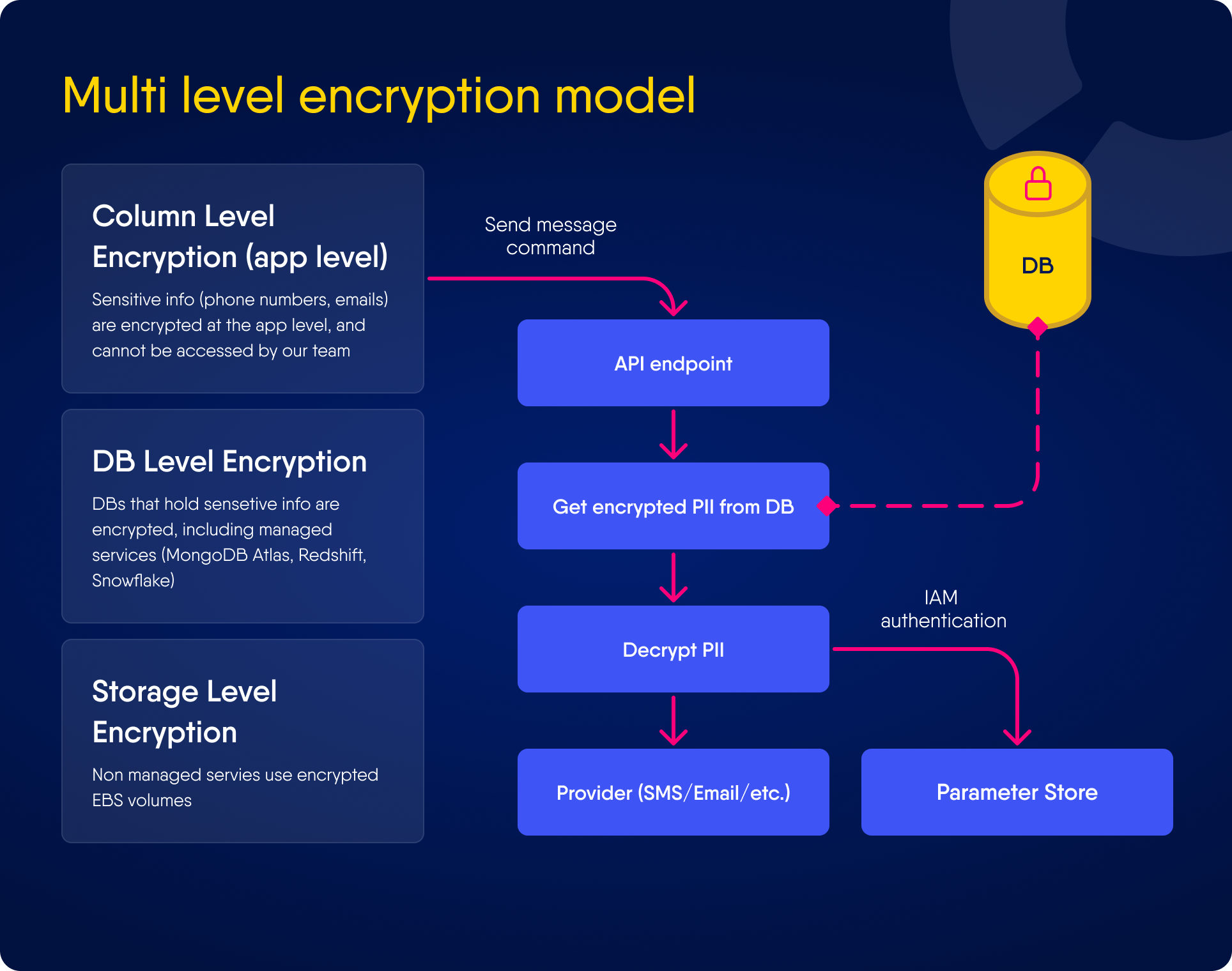
3 Layers Encryption at Rest
-
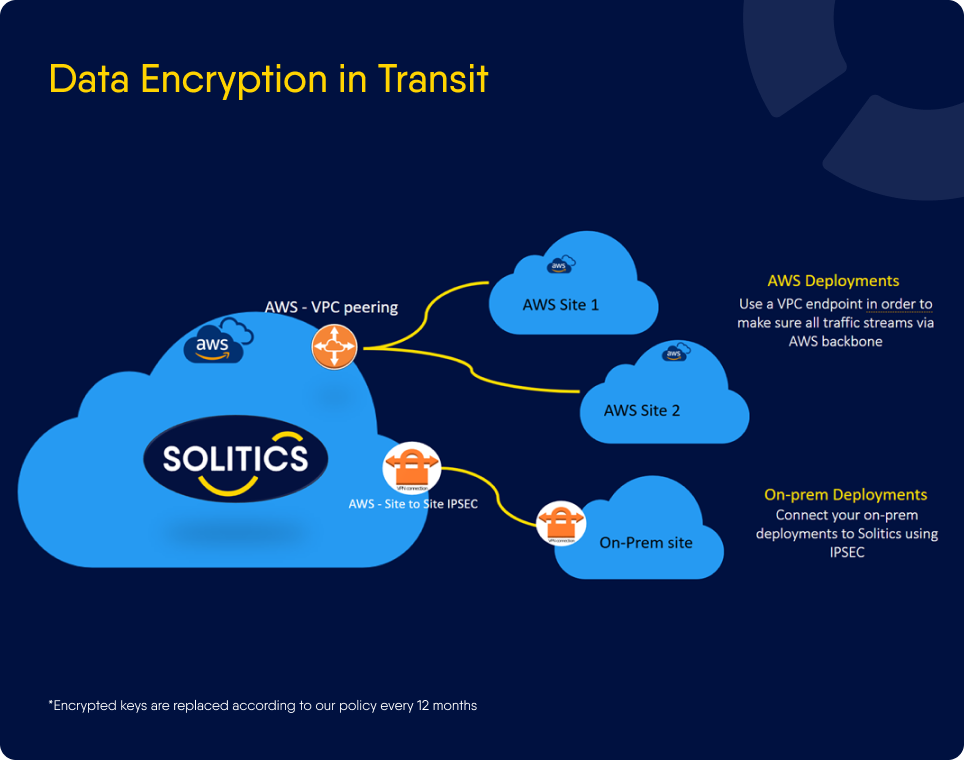
Encryption in Transit
Resiliency
-
Multi A-Z Deployment
-
Continuous Encrypted Backups of the Data
-
Scalable
Data privacy
-
PII Protection Features - Mode 1
-
PII Protection Features - Mode 2
-
Privacy Rights Automation
-
GDPR Embedded Features
-
Member Data Consolidation and Control
Monitoring and support
-
24/7 monitoring of data discrepancies and security threats
-
Best in class support

















You can rely on us
Solitics Security Best Practices
Product security:
Solitics follows security and privacy best practices.
We’ve implemented a combination of policies, procedures, and technologies to ensure that all data is adequately protected and secured.
Product status:
Solitics Data is a managed by cloud integration platform hosted on Amazon Web Services. It operates in AWS EU region. You can read our Solitics Data Security Architecture Overview.
Business continuity
Solitics maintains a business continuity plan regarding how we respond to disruptive events. The plan addresses: data backup and recovery; all mission-critical systems; financial and operational assessments and checklists; alternative communications with customers, employees, and regulators; evacuation plans; alternate physical location of employees; critical suppliers and regulatory reporting.
Security incident response
Security incident response At Solitics, a security incident is any event assessed by our CISO and/or DPO that violates our policies or threatens the security of information systems. We identify incidents through system monitoring, staff reports, or service issues. Incidents, once discovered, are promptly declared, documented, and categorized by their importance—critical, high, medium, or low—based on potential data exposure or resource criticality. Your security matters to us!

